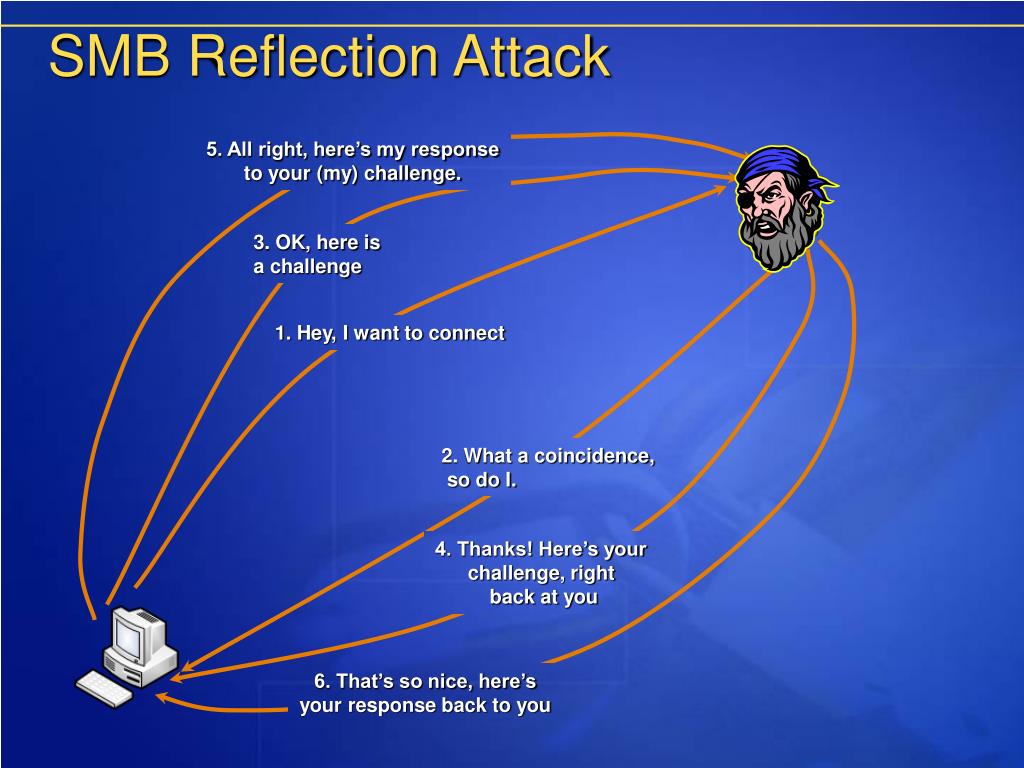
How Does A Reflection Attack Work . in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. When launching an attack, the attacker sends. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. A basic denial of service attack is essentially a traffic flood, designed to exhaust.
from www.slideserve.com
an attacker obtains large quantities of open ports of public network servers as reflectors in advance. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. A basic denial of service attack is essentially a traffic flood, designed to exhaust. When launching an attack, the attacker sends. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user.
PPT Windows Passwords Everything You Need To Know PowerPoint
How Does A Reflection Attack Work reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. When launching an attack, the attacker sends. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user.
From templatelab.com
50 Best Reflective Essay Examples (+Topic Samples) ᐅ TemplateLab How Does A Reflection Attack Work an attacker obtains large quantities of open ports of public network servers as reflectors in advance. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. When launching an attack, the attacker sends. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user.. How Does A Reflection Attack Work.
From crescendowork.com
DEI Reflection Exercises to Make You a Better Manager — Crescendo How Does A Reflection Attack Work When launching an attack, the attacker sends. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. reflection attacks capitalize on mutual. How Does A Reflection Attack Work.
From www.akamai.com
What Is a CLDAP Reflection DDoS Attack? Akamai How Does A Reflection Attack Work A basic denial of service attack is essentially a traffic flood, designed to exhaust. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. an attacker obtains large quantities of open ports of public. How Does A Reflection Attack Work.
From www.slideserve.com
PPT DNS, DNSSEC and DDOS PowerPoint Presentation, free download ID How Does A Reflection Attack Work A basic denial of service attack is essentially a traffic flood, designed to exhaust. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. When launching an attack, the attacker sends. . How Does A Reflection Attack Work.
From www.hhi.fraunhofer.de
Reflection Analysis for Face Morphing Attack Detection How Does A Reflection Attack Work an attacker obtains large quantities of open ports of public network servers as reflectors in advance. A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. reflection attacks capitalize on mutual authentication schemes in order to trick the. How Does A Reflection Attack Work.
From scalehub-offices.com
The power of reflection in the workplace ScaleHub Offices How Does A Reflection Attack Work an attacker obtains large quantities of open ports of public network servers as reflectors in advance. When launching an attack, the attacker sends. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address. How Does A Reflection Attack Work.
From www.thesecuritybuddy.com
Authentication Reflection Attacks and DoS Reflection Attacks Page 2 How Does A Reflection Attack Work let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. reflection attacks capitalize on mutual authentication schemes. How Does A Reflection Attack Work.
From info.menandmice.com
"DNS reflection or DNS amplification attacks" How to secure your DNS How Does A Reflection Attack Work A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. reflection attacks capitalize on mutual authentication schemes in order. How Does A Reflection Attack Work.
From www.slideserve.com
PPT Chapter 7 DenialofService Attacks PowerPoint Presentation How Does A Reflection Attack Work an attacker obtains large quantities of open ports of public network servers as reflectors in advance. When launching an attack, the attacker sends. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. A basic denial of service attack is essentially a traffic flood, designed to exhaust. in reflection. How Does A Reflection Attack Work.
From autoize.com
Defending Against DDoS Reflection Attacks Autoize How Does A Reflection Attack Work in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. A basic denial of service attack is essentially a traffic flood, designed to exhaust. When launching an attack, the attacker sends. an. How Does A Reflection Attack Work.
From www.slideserve.com
PPT Security Handshake Pitfalls PowerPoint Presentation, free How Does A Reflection Attack Work an attacker obtains large quantities of open ports of public network servers as reflectors in advance. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. A basic denial of service attack is essentially. How Does A Reflection Attack Work.
From www.cloudflare.com
Protection et atténuation DDoS avancées Cloudflare How Does A Reflection Attack Work let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. When launching an attack, the attacker sends. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user.. How Does A Reflection Attack Work.
From www.youtube.com
Reflection Attacks YouTube How Does A Reflection Attack Work A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. When launching an attack, the attacker sends. an adversary accomplishes. How Does A Reflection Attack Work.
From carers.ripfa.org.uk
Critical reflection tool Social Work Practice with Carers How Does A Reflection Attack Work an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder. How Does A Reflection Attack Work.
From zhuanlan.zhihu.com
什么是SYN Flood攻击? 知乎 How Does A Reflection Attack Work A basic denial of service attack is essentially a traffic flood, designed to exhaust. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. When launching an attack, the attacker sends. an attacker obtains large quantities of open ports of public network servers as reflectors in advance. reflection. How Does A Reflection Attack Work.
From computersecuritypgp.blogspot.com
Computer Security and PGP Authentication Reflection Attack and DoS How Does A Reflection Attack Work When launching an attack, the attacker sends. A basic denial of service attack is essentially a traffic flood, designed to exhaust. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user.. How Does A Reflection Attack Work.
From network-insight.net
DNS Reflection Attack How Does A Reflection Attack Work in reflection attacks, adversaries spoof a target’s ip address and send a request for information, primarily using the user. A basic denial of service attack is essentially a traffic flood, designed to exhaust. let's start with a brief reminder on how reflection attacks (often called amplification attacks) work. reflection attacks capitalize on mutual authentication schemes in order. How Does A Reflection Attack Work.
From ithelp.ithome.com.tw
[Day26] 攻擊行為-阻斷服務攻擊 Denial of Service attack iT 邦幫忙一起幫忙解決難題,拯救 IT 人的一天 How Does A Reflection Attack Work When launching an attack, the attacker sends. reflection attacks capitalize on mutual authentication schemes in order to trick the target into revealing the secret shared. an adversary accomplishes a reflection attack by sending packets to reflectors with the spoofed address of the victim. in reflection attacks, adversaries spoof a target’s ip address and send a request for. How Does A Reflection Attack Work.